Since September 1, the International Press Institute (IPI) has been battling a targeted and sustained cyberattack. This attack appears to be in retaliation for our advocacy work on behalf of independent media in Hungary, who have faced a wave of similar attacks since this summer.
The attack on IPI began with a series of distributed denial-of-service (DDoS) attacks that initially took our website offline for three days. Our website has since been restored after scaling up security measures. We continue to experience milder DDoS attacks alongside efforts by attackers to breach our website.
This ongoing cyberattack is the most brazen and direct attack on IPI’s online infrastructure in our organization’s history. It reflects a wider and deeply alarming pattern of the abuse of digital tools by malicious actors to attack and silence critical journalists and those who work to defend them.
This cyberattack began just days after we released a statement highlighting a recent wave of DDoS attacks that have downed the websites of dozens of independent media outlets in Hungary over the past five months. In that report, we correctly describe these DDoS attacks as a new form of digital censorship that is further threatening Hungary’s already besieged independent media. We also called on Hungarian law enforcement to identify and hold those responsible to account, and urged greater attention from the European Union.
Evidence of the attack on IPI shows that we have been targeted by the same cybercriminal or criminals behind the ongoing DDoS attacks in Hungary. These attackers left behind a message warning of another attack. We believe this is a deliberate and targeted attack on our organization in retaliation for shining a light on this dangerous new front in the war against Hungary’s independent media.
“While these attacks have disrupted our work, they have only strengthened our resolve,” said Khadija Patel, chair of IPI’s global Executive Board. “We are more committed than ever to our mission of defending press freedom and independent journalism wherever they are threatened. We will continue to stand by independent media in Hungary and around the world.”
Below, we provide a more detailed account of the timeline, scope, and mode of the cyberattack against IPI and what steps we have taken to combat it.
Overview and timeline
DDoS attacks are a type of cyberattack that aims to disrupt websites by overwhelming them with traffic. These attacks are on the rise globally and are increasing in scale and complexity. They also require less technical sophistication and resources to carry out than are necessary to defend against them – creating an advantage for malicious actors.
In our case, these DDoS attacks came in the form of increasingly larger “HTTP flood attacks” that are designed to overwhelm a server with HTTP requests, which ultimately will result in a denial-of-service for normal visitors to a website once the server becomes saturated with requests.
The first wave of requests came on September 1. This occurred two days after the publication of IPI’s report on the Hungarian DDoS attacks, on August 29. This first phase of the attack, which may have been a test to probe our defences, did not manage to knock our website offline, as the security protections from Project Shield (from Jigsaw, a subsidiary of Google) proved to be sufficient.
Then between September 6 and 8, the attackers successfully brought our website down multiple times, increasing the scale of the attack in waves after persistently overcoming security countermeasures put in place by our IT team. On September 8, the size of the attack increased significantly, with 350,000 requests per second.
In response, on September 8 we scaled up our defenses further with security measures offered through Cloudflare’s Project Galileo, which provides cyber defenses by preventing malicious traffic from reaching our servers. These security measures have proven effective at countering the DDoS attacks – which have become much smaller in size – and in keeping our website online. The mode of attack has since shifted towards efforts to gain unauthorized access to our website.
What we’ve learned (so far)
Since the attack started last week, our IT team has begun to evaluate the log data to better understand the source and mode of this attack.
Here’s what we’ve learned so far:
1. The attacks were carried out by means of ordinary web-hosting companies and infrastructure. Malicious hackers often launch DDoS attacks with the use of botnets – or a group of bots – that have been infected with illegal malware that can be controlled remotely to attack a specified target. In this case, the DDoS attack on IPI was carried out using the infrastructure of ordinary web hosting services, including those offered by Amazon AWS, Microsoft Azure, and Google Cloud.
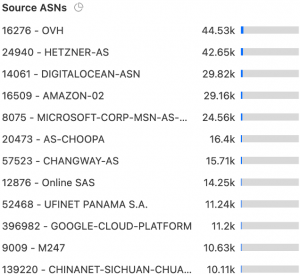
Screenshot from IPI’s Cloudflare dashboard.
This raises critical questions about what mechanisms these private companies have in place to ensure they are preventing and mitigating the abuse of their services to carry out DDoS attacks – and to ensure they are not actually profiting from these abuses. For example, a recent report by the Committee to Protect Journalists highlights how the infrastructure of US-based proxy provider Rayobyte has been deployed to carry out DDoS attacks against Somali Journalist Syndicate, a press freedom group in Somalia). This activity was revealed by Qurium, a Swedish non-profit organization, that has tracked the use of Rayobyte infrastructure in DDoS attacks against a number of media outlets, including on the Nacionale (Kosovo), Kloop (Kyrgyzstan), Peoples Gazette (Nigeria), Bulatlat (Philippines), and Turkmen News (Turkmenistan).
2. The requests were coming from servers in many parts of the world. The attacks came from servers in the US, Germany, Russia, France, Indonesia, Singapore, Japan, China, the U.K., and the Netherlands (see list below).
This list does not tell us much about the source of attack or the actual location of the attacker or attackers because the traffic is constantly rerouted through different countries. But it does illustrate the complexity of fighting these types of attacks.
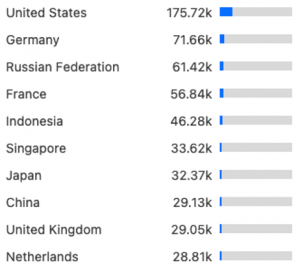
Screenshot from IPI’s Cloudflare dashboard.
3. Attacker is persistent, appears well resourced – and left a message for IPI. What’s notable about this attack is less its size – DDoS attacks can be much larger – than the persistence of the attacker, who responded to each security measure put in place with counterattacks spanning the course of many days. This is one of the clearest indications that it was a targeted attack.While it’s difficult to uncover the source of these attacks, evidence strongly indicates that the attack against IPI is being carried out by the same attacker or attackers that have been targeting independent media sites in Hungary. This attacker or attackers go by the name of “HANO”. While it is not certain what meaning the name might have, if any, Hungarian media have noted that HANO is the Hungarian acronym for a medical condition that results in severe bodily swelling.
The same name has been found in the IPI log data of the attack, and the attacker left IPI a message in English: “see you next time Hano hates u”.

Screenshot from IPI’s Cloudflare dashboard.
As we noted in our report on the DDoS attacks in Hungary, this same attacker has likely targeted dozens of independent media outlets with sustained DDoS attacks over the past five months. This attacker appears to demonstrate knowledge of the Hungarian media landscape and individual journalists, and has also left messages in the code in Hungarian warning of future attacks. Security experts also say the costs associated with this scale and duration of DDoS attacks, at this point continuing over months, also indicates that those responsible are relatively well resourced.
What’s next
At present, the attack on our digital infrastructure is under control and is being closely monitored by our IT team.
In the immediate term, we plan to take the following actions:
a. Notify public authorities. We have filed a report with the cybercrimes unit of the Austrian police as well as with the regular, and provided authorities with log data of the DDoS attack. We will follow up with these authorities to ensure our case is being addressed and investigated. We are also in the process of notifying other relevant authorities in the EU to ensure full accountability for this attack.
b. Notify private companies. We plan to notify the private web hosting companies involved in this attack that their services and infrastructure have been used to carry out an illegal DDoS attack on our systems, and to understand what mechanisms these companies have in place to prevent the malicious use of their services and to address these activities once they are discovered. Private companies must have strong governance and accountability mechanisms in place to ensure that their products and services do not contribute to or exacerbate human rights abuses. This means that these companies must ensure that their services and infrastructure are not being abused by malicious actors to perpetrate attacks on the media and civil society groups. We will follow up to ensure these companies have taken steps to address these abuses.
c. Share data on DDoS attacks with independent security researchers. We will share as much information and data as we can on the attack with security experts and researchers, who can investigate this attack further.
d. Increase our advocacy on digital attacks against journalists and independent media. We plan to re-double our advocacy efforts on this issue, which is a growing challenge facing independent media today. We also hope to increase our support to Hungarian independent media and to IPI members facing cyberattacks.



